Table of Contents
**This is an old revision of the document!**
Virus Scanning Protection
The Enterprise File Fabric prevents the downloading and sharing of malicious files through a ‘scan on write’ approach. As files are uploaded they are scanned. If a virus is detected, the upload fails, and an error is returned immediately to the user or application.
The audit log (for add/update) captures successful and unsuccessful scans and uploads:
File solution-brief.pdf uploaded to My Cloud files/mybucket. Scanned with antivirus ClamAV 0.99.2/24143/
ClamAV is the officially supported virus scanner available for use with the File Fabric. ClamAV is a high performance multi-threaded daemon supporting many file formats including file and archive unpacking.
In High Availability environments each appliance will run a local ClamAV service (as configured by default). Files added outside of the File Fabric, directly to the external storage and discovered through provider synchronization, are not scanned.
Works with:
- Enterprise Appliance (since 1712.00)
Configuration
The virus scanning of uploads is a configuration option for the organization. The option is available when added to the user package.
1. Adding the ClamAV Option to a User Package
To make the ClamAV available as a configuration option for an organization tenant the feature must be added as an 'Extra option' in the User Package.
To make this change, login as the Appliance Administrator (appladmin). From the Main menu (the hamburger icon top right) select 'User Packages’. For the package you want to change select Edit (the pencil icon). Once you’ve selected 'ClamAV Antivirus Integration' choose Save.
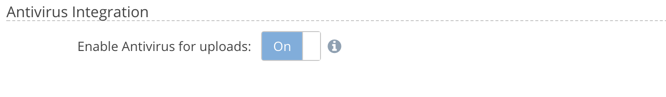
2. Enabling Antivirus Scanning
An Organization Administrator can enable virus scanning for uploads under Organization > Policies > Security:
Troubleshooting
Checking that the ClamAV Service is On
The ClamAV service is preinstalled on the appliance and is enabled and running by default.
To verify ClamAV has been running successfully check the last entries in the log:
$ tail /var/log/freshclam.log ... Fri Feb 2 00:34:21 2018 -> SelfCheck: Database status OK
Use systemctl to verify ClamAV is both enabled (that is, will startup on boot), and running:
$ systemctl status clamd@scan Loaded: loaded (/usr/lib/systemd/system/clamd@scan.server; enabled;... Active: active (running)
If needed, to stop, start, enable, disable or restart run systemctl as root:
systemctl restart clamd@scan
Configuration
ClamAV configuration settings can be found at:
/etc/clamd.d/scan.conf
Checking Virus Signatures are Fresh
The Freshclam application updates the antivirus signature database. It is preinstalled on the appliance and by default is scheduled to run once an hour.
To verify Freshclam has been running successfully check the last entries in the log:
tail /var/log/freshclam.log
To verify the connection to the online database (and update definitions) run as root:
freshclam
By default virus definitions are updated once an hour (see /etc/crontab).
47 * * * * root /usr/bin/freshclam --quiet
Configuration
Freshclam can be configured through the file:
/var/www/smestorage/config/clamd/freshclam.conf
Checking Appliance Integration with ClamAV
This configuration file can be found at:
/var/www/smestorage/public_html/config.inc.php
Make sure the following settings are present:
var $enableantivirus = 1; var $clamavsocketpath = '/var/run/clamd.scan/clamd.sock';
Error: Socket Operation Failed
If the ClamAV service is not running when the user uploads a file the user may see the following message:
Socket operation failed: No such file or directory (SOCKET_ENOENT)
Checking Virus Scans
Verify scans are operational through the audit trail. The policy “Audit File add/update” must be enabled by an administrator under Policies > Security > Audit > Events.
File solution-brief.pdf uploaded to My Cloud files/mybucket. Scanned with antivirus ClamAV 0.99.2/24143/
For a positive match the log looks like:
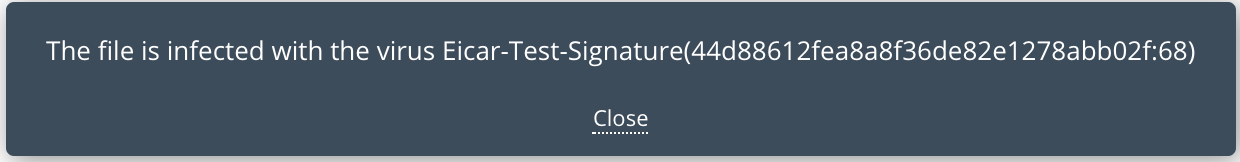
EICAR-testfile.txt failed to upload to myprovider/mybucket/myfolder . Antivirus ClamAV detected Eicar-Test-Signature(44d88612fea8a8f36de82e1278abb02f:68) infection. ClamAV version ClamAV 0.99.2/24211/
For a test virus file see https://en.wikipedia.org/wiki/EICAR_test_file.