Bring Your Own Device (BYOD)
1 Overview
Bring Your Own Device or BYOD as it is often referred to, refers to policies where employees may use their own smartphones, tablet devices and computers to access corporate data. This presents challenges for organizations who want to embrace the flexibility and cost savings of users using their own devices, but also want to ensure they still have “control”. The Access Anywhere has support for controlling BYOD users of which an overview will be given in this Wiki section.
2 Managing User devices
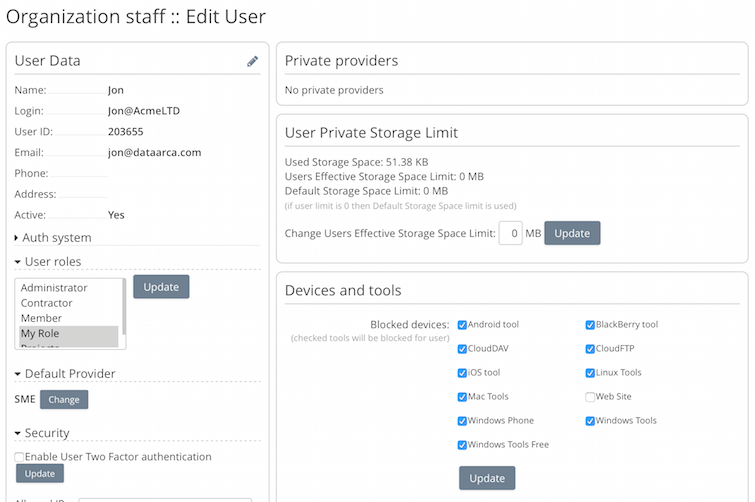
The Cloud Admin controls which devices and access clients that each user of the team can connect from. By default all devices and access clients are enabled.
The Cloud admin can entirely disable a user or just choose to disable access from any of the devices/access clients from the users settings. Clicking the checkbox next to the appropriate device blocks access to that device for that user. This means that if a device is lost even if login details are saved login will be denied.
Blocked devices can easily be seen in the user summary.
3 Secure Access
Our WebDAV implementation (see CloudDAV (WebDAV Protocol)) supports the MobileIron Docs@Work application for accessing repositories.
4 Remote Wipe
We often get asked about 'Remote Wipe', the ability for a device owner or corporate administrator to remove sensitive information without needing to physically access a device.
4.1 Corporate
For a corporate administrator this typically means wiping corporate data and applications when an employee leaves or changes position. We recommend investing in one of many Mobile Device Management (MDM) solutions that support the remote removal of applications (and associated data).
MDM solutions are available from operating system vendors and third-parties. Customers may use for example:
- MacOS: Apple Business Manager
- Windows: Microsoft Intune
We have also had customers use third party solutions including:
4.2 Owner
For a device owner a remote wipe typically means removing all local data, credentials and applications. It's useful when a device has been lost or stolen, or even simply replaced, but is not physically available. In this situation options include:
- MacOS: Remote wipe can be handled at a device level. All this is needed is that iCloud is enabled and Find my iPhone (or iPad) is enabled. Remote wipe can then be executed from a web browser.
- WindowsOS: Windows users might use software that allows remote login to a lost computer.