Table of Contents
Edge Extend Agent for AWS
This guide covers the network configuration of the Edge Extend Agent running on the AWS Cloud in your AWS Account. Once network configuration is complete return to Edge Extend Server to continue setup.
For general documentation see Edge Extend
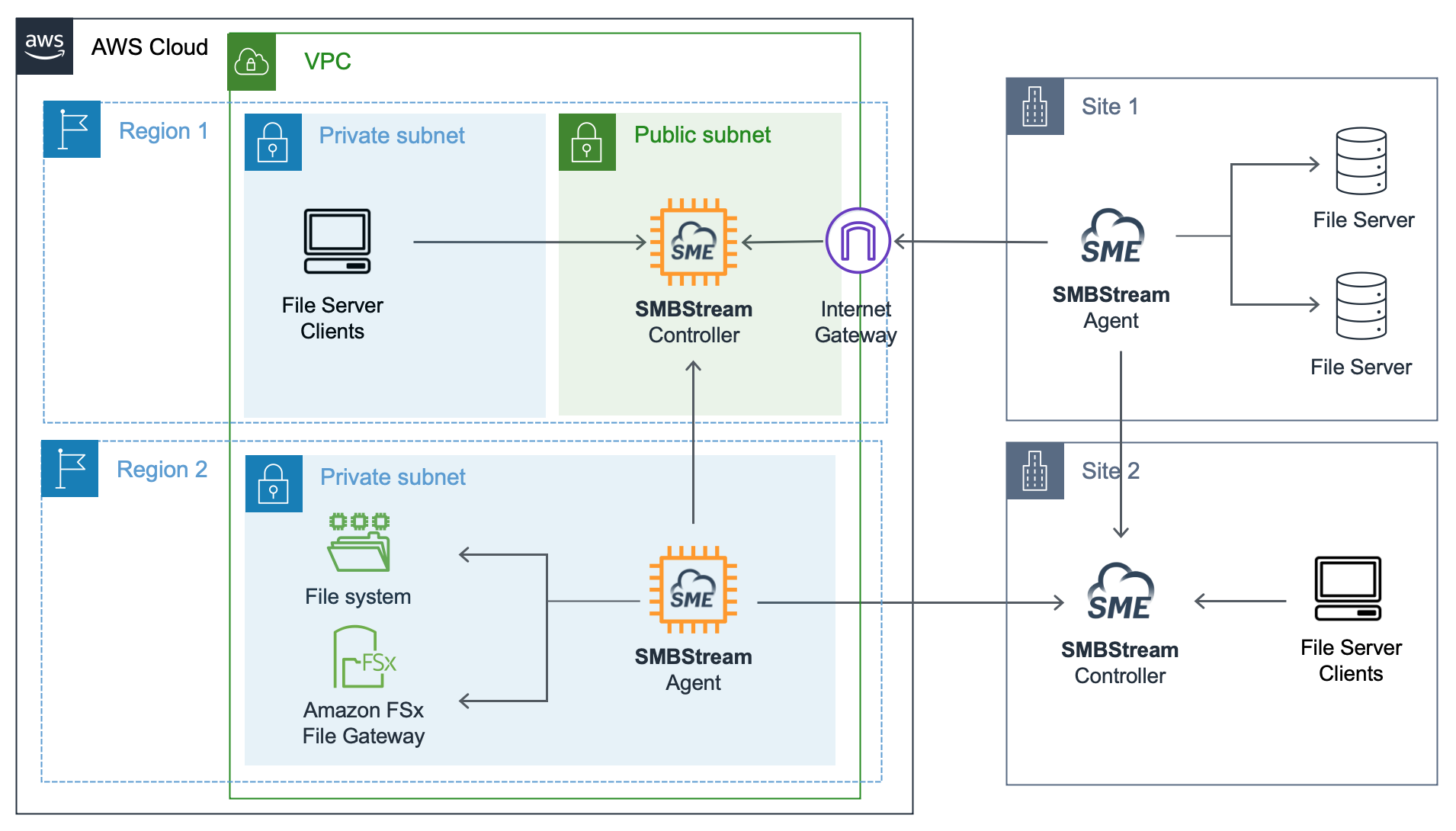
Architecture
Virtual Machine
Each Edge Extend agent is deployed to the AWS as a single virtual machine or instance. Agents connect to a single Edge Extend server, deployed on another region or cloud, through a public endpoint. They will connect using a UDP protocol through port 8445.
Deployment
This guide walks through deploying an Edge Extend agent to your environment. An instance will be launched directly from the AWS Marketplace. Once the instance is running you'll set up the network, and then, after registering the agent with a server, you will complete set up.
Skills Required
This guide is for IT infrastructure architects and DevOps professionals who are deploying an Edge Extend agent on AWS.
To follow this guide a user should have some familiarity with the AWS Console and with a Linux shell.
Time Required
Following this guide, an Edge Extend agent can be deployed in under an hour.
Prerequisites
You will need the following information before you can complete the setup:
- An AWS Account. If you don’t already have an AWS account, create one at https://aws.amazon.com/getting-started/ by following the on-screen instructions.
Security
As with all systems you deploy to the AWS Cloud security responsibilities are shared between you and AWS. AWS is responsible for the host operating system and virtualization layer down to the physical security of the facilities in which the services operate. You assume responsibility for the security of the appliance through configuration and management of specific AWS Cloud services and of the appliance itself. Through the appliance, you can delegate specific application and data security responsibilities to designated users and roles.
For more information:
AWS Identity and Access Management
The agent needs access to any network storage server for which remote access is required.
It does not access AWS services.
Operating System Security
The appliance does not use root or other administrative uses to run internal components. An end-user cannot log in as root – they can use sudo from the user smbstream. A user can log into the smbstream account only by using the SSH key specified during the deployment process. AWS doesn't store these SSH keys, so if you lose your SSH key, you can lose access to these instances.
We will announce high-severity security patches when they are available through a security alert (email). This includes security patches to third-party components we may be using and other remediations.
Customer Sensitive Data
Edge Extend provides a number of preventative and detective mechanisms to protect customer data. For more information see Edge Extend Security.
Data Encryption
The Access Anywhere encrypts data in motion and provides a number of options for encrypting data at rest in addition to that provided by the storage service.
- Amazon S3 server-side encryption can be enabled
- Folder encryption, where data is sent encrypted to the storage
- Personal encryption where data is encrypted by the client before Access Anywhere.
For more information see Edge Extend Security.
Security Groups
A security group acts as a firewall that controls the traffic for one or more instances. When you launch an instance, you associate a security group with it. You add rules to the security group that allow traffic to or from the instance. You can modify the rules for a security group at any time.
Launch
AWS Marketplace
To launch directly from the marketplace select Edge Extend Agent.
Select “Continue to Subscribe”.

Review terms and select “Continue to Configuration”.

Select your preferred Region and then select “Continue to Launch”

This page allows you to launch the instance directly from this webpage, or through the EC2 launch instance wizard.

Leave the setting as Launch from Website (Recommended). Instructions for launching from EC2 instead are provided in the section Launch Through EC2.

Launch from Website (Recommended)
Review Configuration details:
- EC2 Instance Type: t3.small
- Memory: 2 GiB
- CPU: 2 virtual cores
- Storage: EBS Only
- Network Performance: Up to 5 Gigabit Ethernet
- VPC Settings: (default)
- Subnet Settings: (default)
Security Group Settings
Select “Create New Based on Seller Settings”.

Create New Security Group
Add a name and description.
Do NOT change the Source (IP or Group) to “My IP” as this setting incorrectly assigns an internal AWS IP address.
Select “Save”.

Key Pair
Amazon EC2 uses SSH-2 RSA keys for SSH which is required to complete the configuration. A public/private key pair can be assigned or created.
Choose an existing Key Pair or create a new one.

Launch
Select the “Launch” button to deploy.

Select EC2 Console to see the instance running in the region you selected.
Add a Name by clicking in the empty Name box and entering “Edge Extend Agent”.
Jump to the next step Configuration.
Launch through EC2
If you did not “Launch from the website”, follow these steps to launch the instance.
Step 1. Choose an Amazon Machine Image (AMI)
- From the AWS Marketplace click Edge Extend Agent.
- Then click Launch.
Step 2: Choose an Instance Type
Minimum recommended settings are:
- vCPUs - 2
- Memory - 2 GB
- Disk - 40 GB (SSD)
This corresponds to a t3.small.
For example,
| Family | Type | vCPUs | Memory (GiB) | Instance Storage (GB) | Network | Notes |
|---|---|---|---|---|---|---|
| t3 | t3.small | 2 | 2 | EBS Only | Up to 5 Gigabit Ethernet | Recommended |
Step 3: Configure Instance Details
Check the following setting:
- Auto-assign Public IP - set to Enable
Step 4: Add Storage
Accept the defaults, for example:
| Volume Type | Device | Snapshot | Size (GbB) | Volume Type | Delete on Termination |
|---|---|---|---|---|---|
| Root | /dev/xvda | snap-xxx | 40 | [General Purpose SSD (gp2] | Yes |
You might wish to change “Delete on Termination” to False to prevent your instance from being accidentally terminated through Amazon EC2.
Step 5: Add Tags
No changes, select Next: Configure Security Group
Step 6: Configure Security Group
Choose the default, a new security group with one rule.
| Type | Protocol | Port Range | Source | Description |
|---|---|---|---|---|
| SSH | TCP | 22 | Anywhere 0.0.0.0/0, ::/0 | SSH for initial configuration |
Step 7: Review Instance Launch
Select [Launch] to bring up the dialog to choose or create a public/private key pair that will allow you to SSH into the instance.

Select Launch Instances.
View Instances
Select View Instances and wait a few minutes until the Status Checks are complete.
Configuration
SSH Access
The instance can now be accessed at this IP address using a standalone SSH client and the Key Pair you assigned. The username is smbstream. For example:
ssh -i "AccessAnywhere.pem" smbstream@34.194.216.200
(If the command freezes check your Security Group allows SSH access (port 22) for your IP address.)
Check that you can become root.
sudo bash
This will be required to complete the configuration.
More information on connecting via SSH can be found in the AWS Console. Select the instance in the Instances view and click Connect.
Next Steps
Once network configuration is complete return to Edge Extend Server to continue agent setup.