Adding / Managing Users
last updated on March 16, 2022
Organizations using an Access Anywhere installation are able to allow users to sign in to their organisation.
The Access Anywhere supports a few identity sources for an organisation.
- Built-in identity source
- Active Directory identity source
- SAML identity source
Administrators can, and do, have the flexibility to use one or more of the above identity sources within the context of a single organisation. This allows customers to federate multiple identity sources, as well as providing, if required, access to users who are not part of an existing domain or realm.
This document covers how users can be managed from the built-In identity source.
If you are interested in how our integration with your other identity sources works, please see Identity and Access Management
Adding new users (web)
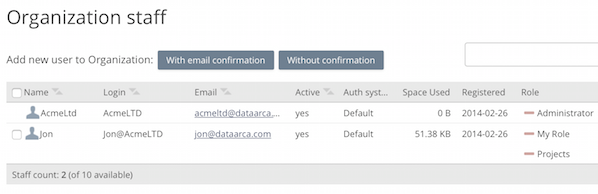
New users can be added by the Team Administrator after logging into team account as the Administrative user and choosing the 'Users' option from the Organization options on the right sidebar.
User names can contain any displayable characters except '<' and '>'.
By default, when a user a is added, each user is given private storage space on the primary storage provider (ie. the storage provider that is set as default). Only the user can access this space and if the amount of storage space given needs to be controlled this can be done using user quotas.
If the Admin requires access to private user space then a different way of setting up user space can be used by creating shared folders that only the user and the Admin has access to.
Bulk users can be added by choosing to open either a .csv or .xls file that contains users in the form of Name, Login, Email.
As a user requires a 'user name' and an email address, in the event that a service account is being used for a user that does not have an email address consider using the User Principle Name (UPN) i.e the name of a system user in an email address format.
User Count Limits
As of version 2106 Access Anywhere enforces numeric limits on three kind of user accounts:
As described in the following sections, the number of users is controlled by a combination of the numbers in the license key, the user limits in User Packages and org.-specific overrides of the User Package numbers.
Personal Accounts
- Has its own control number in the license key.
- No package user limit considerations.
Organization Accounts
- Includes org. admins and org. members.
- Has its own control number in the license key.
- Bound per org. by user limit if set on org. admin user record else by package limit.
- Where applicable, package limit is applied per org. using the package.
- License key limit applies to total cross all orgs.
- Inactive users don’t count against this limit.
External Accounts
- Has its own control number in the license key.
- User limit in package applies.
- Control number in key limits total across all orgs.
- Allocated first-come-first-served.
- Inactive users don’t count against this limit.
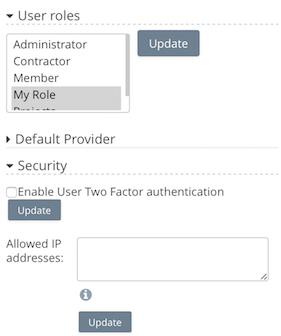
User Roles
If more than one admin is required for Access Anywhere, another user can have his role changed to that of an Admin. Once nominated a user with the Admin role will be able to do anything a the main Administrator can do except to promote other users to also be an administrator.
Security
User accounts that are created within Access Anywhere using the Built-in identity source are local users. Their credentials are stored in a hashed and salted manner using SHA-256. 2-factor authentication can be enabled for users of the platform to further enhance security.
The Access Anywhere also supports an integration with the KeyCloak Identity platform. Please contact us if you would like to learn more.
Administrators Can Log In as Other Users
To help administrators provide support to users, Access Anywhere optionally allows administrators to log in as other users. Specifically:
- If impersonation is enabled by the appliance administrator in Site Functionality then she can log in as the organization administrator or as any member in any organization.
- If impersonation has been enabled by the appliance administrator in the package assigned to an organization then the organization administrator or any member with the Administrator role can log in as any member of the organization.
In both cases the login is recorded in the audit logs.
To log in as a different user, the administrator first logs in as herself and then clicks on the key icon in the row representing the user on on the Users page (for appliance administrators):
or the “Organization staff” (for organization administrators):
Role Permissions and Users Maintenance
- The organization administrator can create and remove users and assign roles to members and remove roles from members.
- Members with the “Administrator” role can create and remove users and assign roles to members and remove roles from members except that they cannot assign the Administrator role.
- Members with the “create users” role permission can create and remove users but they cannot assign roles to members or remove roles from members.
- Members with the “manage users” role permission can remove users but they cannot create users and they cannot assign roles to members or remove roles from members.
- Members with the “manage roles” role permission can assign roles to members and remove roles from members except that they cannot assign the Administrator role
Access Control
For user Access Control, please see the User Access Controls section of the Cloud File Server Wiki.
Deleting users
Information about deleting users can be found here.