Identity and Access Management
last updated on July 10, 2023
Nasuni Access Anywhere Identity and Access Management (IAM) enables users to configure and manage secure access to resources and services.
Capabilities include:
- Integration with external identity providers (IdPs)
- Support for single-sign-on (SSO)
- Several types of multi-factor authentication (MFA)
- Fine-grained, user and role-based (RBAC) hierarchical permissions
- Audit trail of configuration changes and access to resources
See Also:
Authentication Services
Users can be authenticated against the internal user database or any directory service. Nasuni Access Anywhere includes out of the box support for Active Directory, and services that support SAML. Once authenticated clients use the authentication token for the remainder of the session.
Directory services are managed by an Organization administrator under Organization > Auth Systems. Multiple auth systems can be configured.
See Also:
Login Policies
Login policies can be managed under Organization > Policies > Security:
- Two-factor Authentication with the options of Google Authentication, an emailed code, or a shared secret supported.
- Require SSL
- Whitelist IP addresses
- Force strong passwords
- Suspend account after N failed login attempts
- Support long session for File Manager (“Remember Me”)
- Support auto-login from client apps ## Adding Users (Members) to an Organization
Users are managed per organization. Users can be added in many ways, more commonly manually, imported from a directory service, or created on first login (based on an LDAP role for example).
A user requires a 'user name' and an email address to be created. In the event that a service account is being used for a user that does not have an email address consider using the User Principle Name (UPN) i.e the name of a system user in an email address format.
See Also:
Authorization & Roles
Nasuni Access Anywhere uses both user-based and role-based access controls (RBAC).
Roles are managed per organization and may be created and managed within Nasuni Access Anywhere, or synchronized with an external Authentication System. See Organization > Roles.
Organization Permissions
Users have permissions to perform different activities at the organization level based on the roles they are assigned.
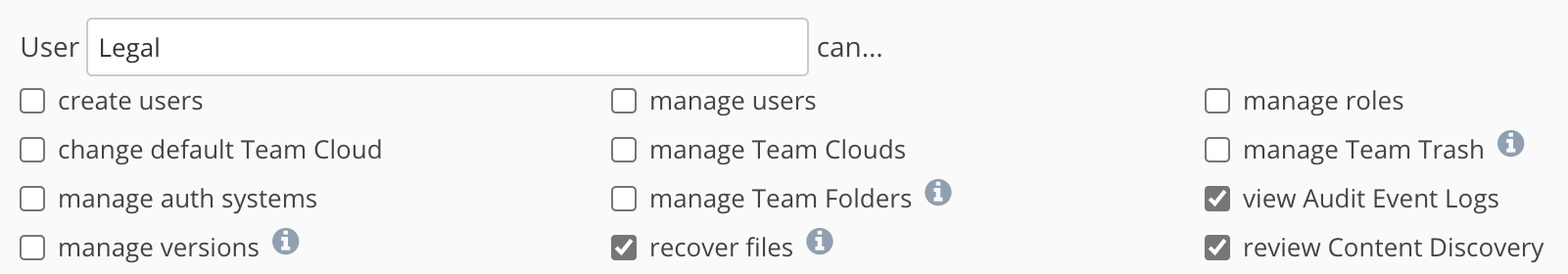
For example, users with the “Legal” role are able to view the Audit Event logs“ if that role has that capability checked:
Resource Permissions
Users have access to resources (files and folders) based on access controls assigned to or inherited by the folder. Permissions can be assigned by user, role or both.
See Also:
Storage Access
If a storage provider supports OAuth, which is a mechanism to connect to a Cloud Provider without revealing password details, then Nasuni Access Anywhere uses this delegation mechanism to access the resource. For storage providers that don't use OAuth, authentication details are stored encrypted. The key to un-encrypt is stored on a key server and we do this when we need to on a per session basis.