Table of Contents
Getting Started with AWS Cloud
Last Updated: March 23, 2023

Why AWS (Amazon Web Services)?
AWS customers are using Nasuni Access Anywhere to take advantage of the high durability, scalability and low cost of AWS Cloud Services.
Overview
This Getting Started with AWS guide provides step-by-step instructions for deploying your own Access Anywhere Server on the AWS Cloud.
Applies to: Version 2301.0
Features
The server indexes and allows interacting with your storage as a single global file system. You can add multiple Nasuni Filers. The content of your data is not copied.
Features include:
- Search across storage by name, metadata, and keyword (content search)
- Remote and at-home users can access from the desktop apps or the web
- Data access/stored in native format - no vendor lock-in
- Add security to object storage with SSO, ACLs, and 2FA.
- Comprehensive audit trail
Costs
You are responsible for the cost of the AWS services used by deploying this solution. This includes the compute instances and other AWS services to which the platform is deployed and any ingress, egress, and storage fees for metadata and data accessed through the platform.
This is an AWS pricing model based on a single node deployment with 1 TB of storage.
| Service | Monthly | First Year | Configuration summary |
|---|---|---|---|
| Amazon EC2 | ~$245.00 | ~2940.00 | Operating system (Linux), Quantity (1), Pricing strategy (EC2 Instance Savings Plans 1 Year No Upfront), Disk (150 GB), Instance type (c6i.2xlarge) |
| S3 Standard | 24.09 | 289.08 | S3 Standard storage (1 TB per month) |
| Data Transfer | 8.91 | 106.92 | DT Inbound: Not selected (100 GB per month), DT Outbound: Internet (100 GB per month) |
| Amazon Elastic IP | 0.00 | 0.00 | Number of EC2 instances (1), Number of EIPs per instance (1), Number of EIP remaps (0) |
| TOTAL | 121.33 | 1455.96 | USD |
Architecture
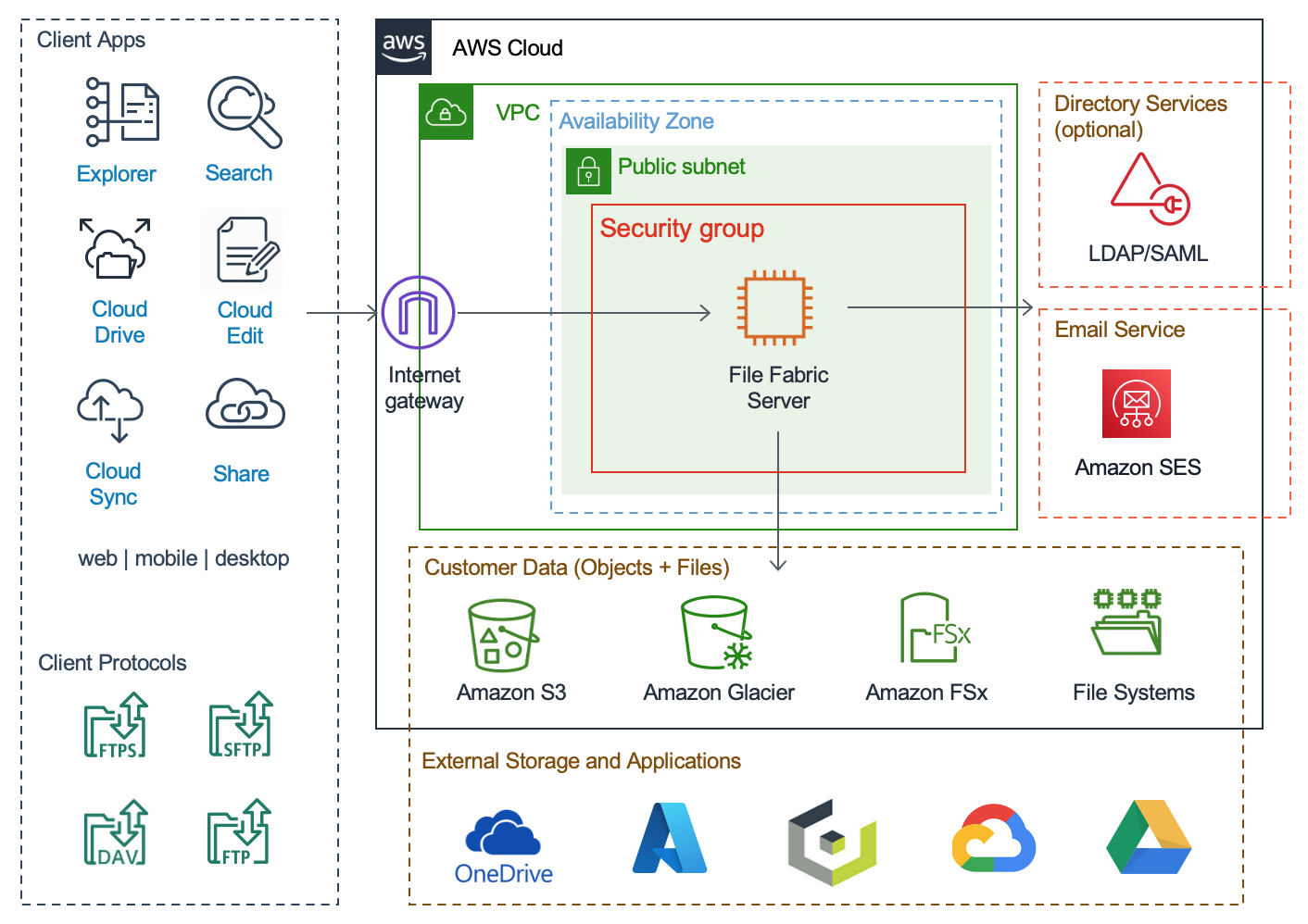
Single VM Deployment
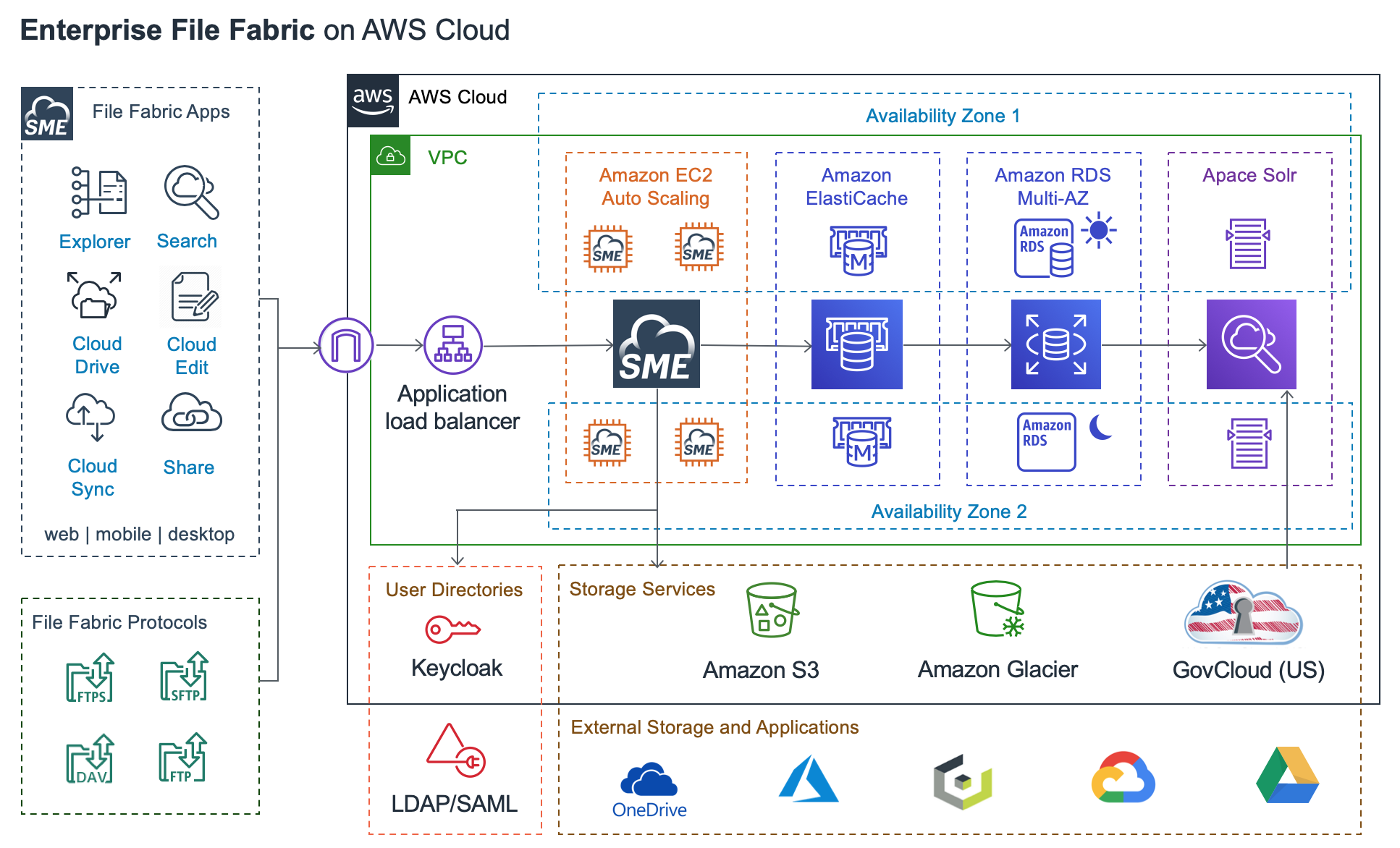
Multiple VM Deployment
The solution may also be deployed in a multi-AZ environment with multiple virtual machines and external databases.
Please contact support for more information on setting up multi-node deployments on the AWS Cloud.
For production deployments see also Architecture and Sizing Guide.
AWS Components
The platform uses the following AWS services:
- Amazon EC2 – The Amazon Elastic Compute Cloud (Amazon EC2) service enables virtual machine instances to be launched with a variety of operating systems. The server is available as a virtual machine image.
- Elastic IP Address - An Elastic IP address is a public IPv4 address, reservable through AWS. It can be mapped dynamically to an instance, allowing instances to be changed without affecting their public address. They also allow mapping to a DNS record for your domain.
- Amazon Simple Email Service (Amazon SES) - Amazon SES is an email service that may be used by the solution for sharing links with other users and receiving notifications.
The solution may also use the following AWS storage services:
- Amazon S3 - Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry-leading scalability, data availability, security, and performance.
Deployment
This guide walks through deploying the Access Anywhere Server to your environment as a single-instance software appliance. You'll have the ability to choose the target region and size the instance for your requirements. After the appliance is started you'll set up the network, and then with the creation of an Organization, you will add storage and users.
Skills Required
This guide is for IT infrastructure architects and DevOps professionals who are deploying the solution on AWS.
To follow this guide a user should have some familiarity with the AWS Console and with a Linux shell. They may require support from a network administrator to create a DNS record, and from an IT administrator if a corporate SSL certificate is required.
Time Required
Following this guide, the Access Anywhere Server platform can be deployed in under an hour.
Prerequisites
You will need the following information before you can complete the setup:
- An AWS Account. If you don’t already have an AWS account, create one at https://aws.amazon.com/getting-started/ by following the on-screen instructions.
- A domain name (recommended).
- A Nasuni Account with access to a Nasuni Access Anywhere Serial Number.
- Outbound mail relay information (recommended).
- Default storage system connectivity details - for example, Amazon S3 (required)
- An Active Directory service account if you are connecting to AD (optional).
Security
As with all systems you deploy to the AWS Cloud security responsibilities are shared between you and AWS. AWS is responsible for the host operating system and virtualization layer down to the physical security of the facilities in which the services operate. You assume responsibility for the security of the appliance through configuration and management of specific AWS Cloud services and of the appliance itself. Through the appliance, you can delegate specific application and data security responsibilities to designated users and roles.
For more information about security on AWS, visit the AWS Security Center. For more information about security see Nasuni Access Anywhere Security.
AWS Identity and Access Management
Following the security principle of least privilege, we recommend that you use two “IAM user” accounts, one with access to EC2 services, and a second with access to Amazon S3 services. They should not be root users. You may also create these users in separate AWS Accounts.
You should assign permissions through groups and assign them to users as needed. For example:
- SME-Admin - The ability to create Amazon EC2 services through the AWS Console.
- SME-Storage - The ability to access Amazon S3 storage (optional)
SME-Admin
For deploying to EC2 we recommend the following policies:
- AmazonEC2FullAccess
- SupportUser
Amazon S3 Storage
The doc page on adding Amazon S3 provides instructions for obtaining access credentials and using a custom policy to limit access to what is needed. Public access is not required. See Amazon S3 Storage
Operating System Security
The application does not use root or other administrative uses to run internal components. An end-user cannot log in as root – they can use sudo from the user smeconfiguser. A user can log into the smeconfiguser account only by using the SSH key specified during the deployment process. AWS doesn't store these SSH keys, so if you lose your SSH key, you can lose access to these instances.
The appliance can be updated with respect to security patches outside of our regular release cycle with the following command:
yum install yum-plugin-security # If automating you can add the "-y" option
We will announce high-severity security patches when they are available through a security alert (email). This includes security patches to third-party components we may be using and other remediations.
Customer Sensitive Data
The platform provides a number of preventative and detective mechanisms to protect customer data. For more information see Nasuni Access Anywhere Security.
Data Encryption
The solution encrypts data in motion and provides a number of options for encrypting data at rest in addition to that provided by the storage service.
- Amazon S3 server-side encryption can be enabled
- Folder encryption, where data is sent encrypted to the storage
- Personal encryption where data is encrypted by the client before sending to the platform.
For more information see Nasuni Access Anywhere Security.
Security Groups
A security group acts as a firewall that controls the traffic for one or more instances. When you launch an instance, you associate a security group with the instance. You add rules to the security group that allow traffic to or from the appliance. You can modify the rules for a security group at any time.
Launch
Launch through EC2
Step 1. Choose an Amazon Machine Image (AMI)
- Choose the AMI that was shared with you by Nasuni.
- Then click Launch.
Step 2: Choose an Instance Type
Minimum recommended settings are:
- 8 vCPUs
- 16 GiB memory
- 200 GB Storage
For example,
| Type | vCPUs | Memory (GiB) | Instance Storage (GB) | Network | Notes |
|---|---|---|---|---|---|
| c6i.2xlarge | 8 | 16 | EBS Only | Up to 12.5 Gigabit Ethernet | Recommended |
Step 3: Configure Instance Details
Check the following setting:
- Auto-assign Public IP - set to Enable
Step 4: Add Storage
Accept the defaults, for example:
| Volume Type | Device | Snapshot | Size (GbB) | Volume Type | Delete on Termination |
|---|---|---|---|---|---|
| Root | /dev/sda1 | snap-xxx | 200 | [General Purpose SSD (gp2] | Yes |
You might wish to change “Delete on Termination” to False to prevent your instance from being accidentally terminated through Amazon EC2.
You can also encrypt the root volume here.
Step 5: Add Tags
No changes, select Next: Configure Security Group
Step 6: Configure Security Group
Create a new security group for “Access Anywhere” with four settings:
| Type | Protocol | Port Range | Source | Description |
|---|---|---|---|---|
| SSH | TCP | 22 | My IP | SSH for initial configuration |
| Custom TCP Rule | TCP | 8080 | My IP | Installation website (temporary) |
| HTTPS | TCP | 443 | Anywhere | Main website |
| HTTP | TCP | 80 | Anywhere | Redirects to the main website |
If you will be accessing the server using FTP/FTPS or SFTP you'll need to add additional ports.
Step 7: Review Instance Launch
Select [Launch] to bring up the dialog to choose or create a public/private key pair that will allow you to SSH into the instance.
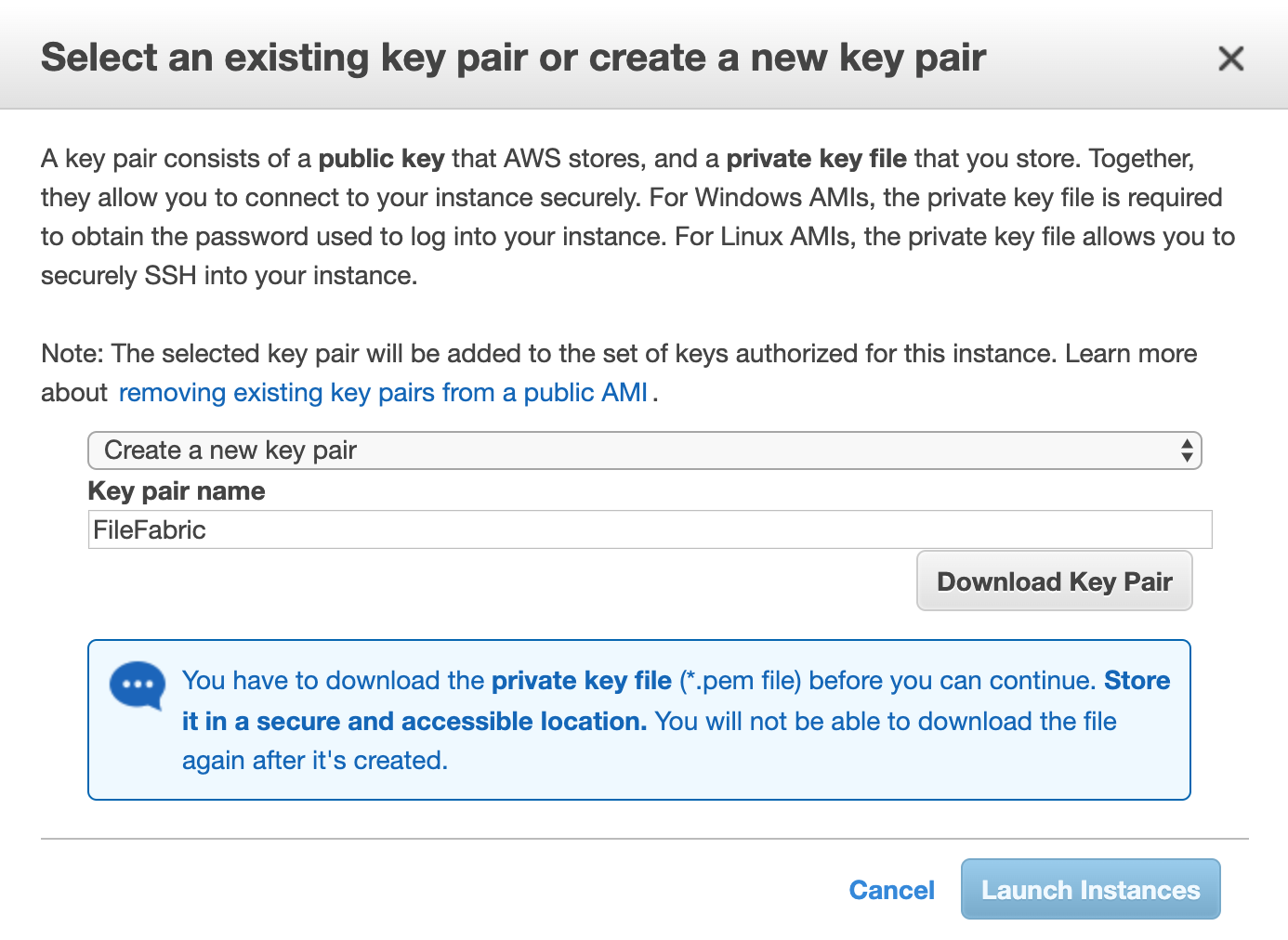
Select Launch Instances.
View Instances
Select EC2 Console or View Instances and wait a few minutes until the Status Checks are complete.
Add Name
Add a name for your instance such as Nasuni Access Anywhere.
Configuration
Configure Public Endpoint
Applications access the server through a public endpoint, a fully qualified domain name that resolves to a public IP address. For single node deployments on AWS Cloud we recommend requesting an AWS Elastic IP Address and associating that with the appliance. You'll also generate a trusted SSL/TLS certificate for that address from the appliance itself.
Associate Elastic IP address
To add a public IP address with the instance from within the AWS Console navigate to Elastic IPs. You should be in the same region as the instance you deployed.
Select Allocate Elastic IP address and Allocate to reserve the IP Address.
Then choose Actions > Associate Elastic IP address to hook it to the instance you just created. Choose Associate to complete.
SSH Access
The instance can now be accessed at this IP address using a standalone SSH client and the Key Pair you assigned. The username is smeconfiguser. For example:
ssh -i "AccessAnywhere.pem" smeconfiguser@34.194.216.200
(If the command freezes check your Security Group allows SSH access (port 22) for your IP address.)
Check that you can become root.
sudo su -
This will be required to complete the configuration.
More information on connecting via SSH can be found in the AWS Console. Select the instance in the Instances view and click Connect.
SSL Configuration (Recommended)
The appliance is configured, by default, with DHCP and a self-generated untrusted SSL certificate.
In order to use the client tools (desktop and mobile applications) over SSL you will need a trusted SSL certificate and a fully qualified domain name (FQDN).
Disabling SSL (Not Recommended)
If you do NOT wish to use SSL for the trial you can disable it.
- Log in as the Appliance Administrator as per the instructions below.
- Navigate to Settings > Site Functionality
- Set Always use HTTPS to No.
- Set Generate secure server-side links to No.
- Select Update options at the bottom of the page.
Create DNS entries
Choose three fully qualified domain names (FQDNs). For example:
- files.example.com - Domain name (service endpoint and website)
- files-webdav.example.com - used for WebDAV service
Add DNS type A records that point these domain names to the appliance IP Address. For example,
| Type | Name | Value |
|---|---|---|
| A | files | 35.188.82.62 |
| A | files-webdav | 35.188.82.62 |
Verify that Public DNS records are set up correctly:
curl -L -k http://files.example.com | head curl -L -k http://files-webdav.example.com | head
These commands should resolve the domain name, connect to port 80, get redirected to port 443 and return (part of) the web login page:
<!DOCTYPE html> <html lang="en" class="for-guest"> <head> <!-- title --> <title>Home | Nasuni Access Anywhere Server</title> <meta content="text/html; charset=utf-8" http-equiv="content-type"/> <meta http-equiv="X-UA-Compatible" content="IE=EDGE,IE=11,chrome=1"/> <meta name="viewport" content="width=device-width, initial-scale=1.0, maximum-scale=1.0, user-scalable=no"/>
Change Hostname
To update the appliance with the FQDN change to the root user by issuing “sudo su -“ with SSH.
Change the hostname to your FQDN by editing /etc/hostname. For example,
echo "files.example.com" > /etc/hostname
Start NAA Config Server
If you are logged in as root leave root privilege:
[root@ip-10-0-0-192 smeconfiguser]# exit
As the smeconfiguser start the configuration server by typing smeconfigserver. You should see a confirmation that the config server is running:
[smeconfiguser@ip-10-0-0-192 ~]$ smeconfigserver Please contact me with a browser on port 8080 Hit Ctrl+C when work is done
Now open your browser to:
http://<your_ip>:8080
Configure Hostname Settings
Here you only need to configure the three domain names. Click “Hostname Settings”.
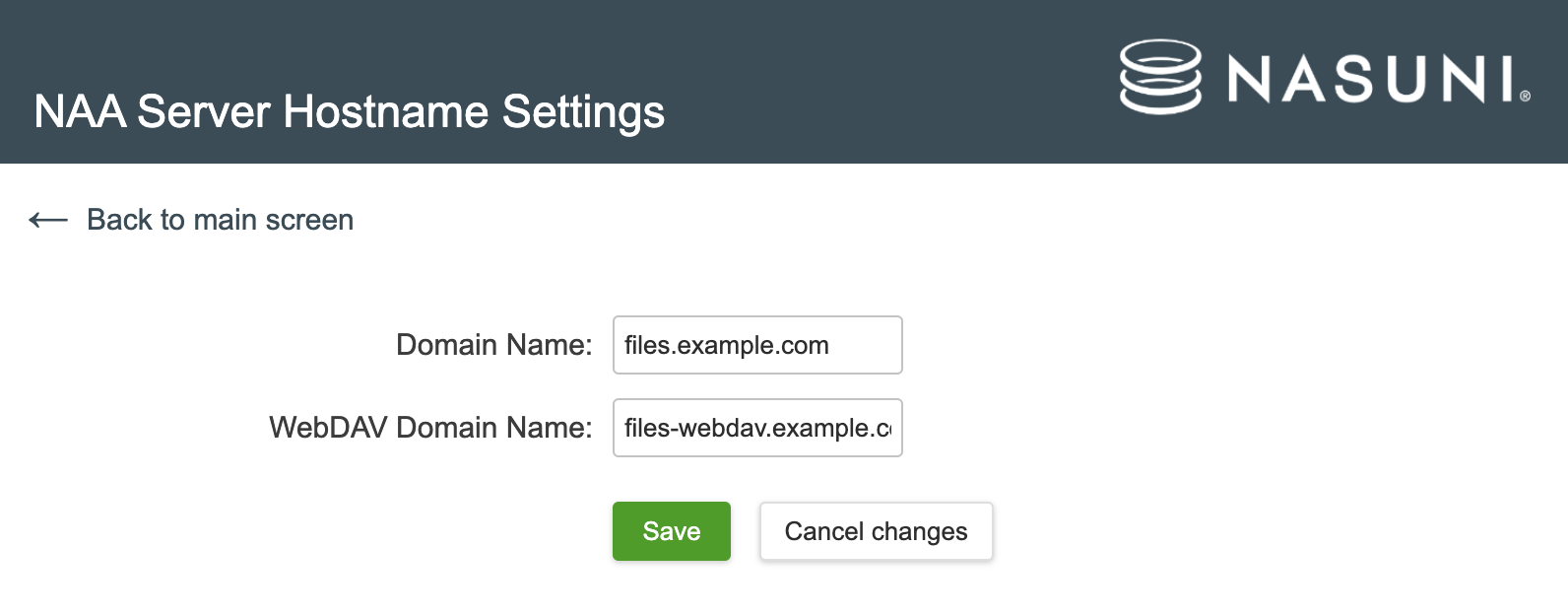
After Saving go to the “Overview” page and scroll down to the bottom to “Apply”. No other changes are required for the appliance on AWS.
You must now reboot the server. Stop the Config Server by typing Control-C in the terminal window.
Change to root and reboot the server.
$ sudo su - # reboot
SSL Certificates
The appliance includes an untrusted SSL certificate.
To create a trusted SSL/TLS certificate associated with your domain see TLS/SSL Certificates.
Configure Appliance
Open a browser to the domain name you assigned, for example:
https://files.example.com
If you haven't set a domain name, use your external IP address:
https://3.234.139.146
You'll see the following login page:
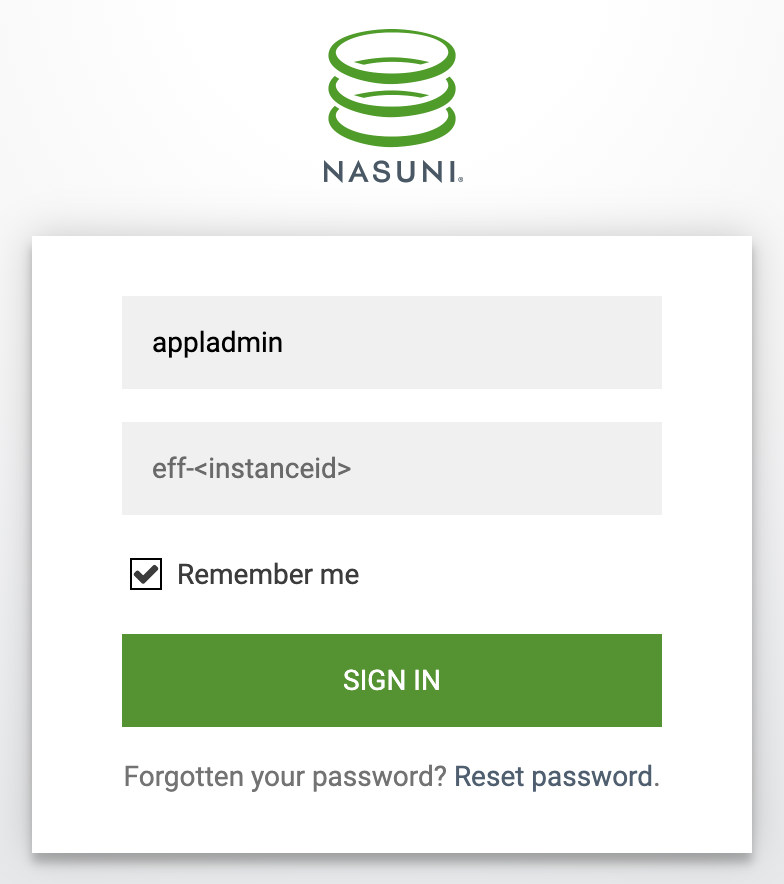
Log into the appliance as appladmin with a password generated from the AWS instance ID:
User name: appladmin Password: eff-<Instance ID>
License Activation
Register your site key under Settings > Account Status & License Key.
For more information see Activating your License.
Change Admin Password (Optional)
Select “Password/Login” from the Main Menu to change the Appliance Administrator password. After you select “Update password” you will be logged out and need to log back in.
Outbound Email (Recommended)
An SMTP server is used by the appliance to send registration and notification emails to users. It can be configured under Settings > Email & Filebox.
If you do not configure an email server remember not to use email notifications when adding users.
To configure an email server see SMTP Configuration.
Change Appliance Admin Email
With an SMTP server configured you can change the email of the Appliance Admin. Go to the main menu (Hamburger icon) to Password/Login.
You can also set up Two Factor Authentication (2FA) for the Appliance Admin from this screen.
Server Notification Email
Server errors and a daily report are sent to a notification email that must be configured by the Appliance Administrator. The default is not to email reports.
The “Notification Email” setting is on the “SMTP and Filebox Configuration” page that can be found via the menu “Email and Filebox”.
Systems Monitoring
For information on general systems monitoring see Systems Monitoring.
Server Notifications
Configure Server Notifications to be emailed a short report on the server status each day.
Amazon CloudWatch Alarms
Use the EC2 Status Checks to monitor CPU usage, the primary metric to monitor resource utilization.
Installing the CloudWatch agent will allow you to other key metrics through CloudWatch as well. Follow the installation instructions for CentOS via the command line and run “yum install collected” before you begin.
This is a CloudWatch agent configuration file: /opt/aws/amazon-cloudwatch-agent/bin/config.json
{
"agent": {
"metrics_collection_interval": 60,
"run_as_user": "cwagent"
},
"logs": {
"logs_collected": {
"files": {
"collect_list": [
{
"file_path": "/var/www/smestorage/sitelogs/logits.txt",
"log_group_name": "logits.txt",
"log_stream_name": "{instance_id}"
}
]
}
}
},
"metrics": {
"append_dimensions": {
"AutoScalingGroupName": "${aws:AutoScalingGroupName}",
"ImageId": "${aws:ImageId}",
"InstanceId": "${aws:InstanceId}",
"InstanceType": "${aws:InstanceType}"
},
"metrics_collected": {
"collectd": {
"metrics_aggregation_interval": 60
},
"cpu": {
"measurement": [
"cpu_usage_idle",
"cpu_usage_iowait",
"cpu_usage_user",
"cpu_usage_system"
],
"metrics_collection_interval": 60,
"totalcpu": false
},
"disk": {
"measurement": [
"used_percent",
"inodes_free"
],
"metrics_collection_interval": 60,
"resources": [
"*"
]
},
"diskio": {
"measurement": [
"io_time",
"write_bytes",
"read_bytes",
"writes",
"reads"
],
"metrics_collection_interval": 60,
"resources": [
"*"
]
},
"mem": {
"measurement": [
"mem_used_percent"
],
"metrics_collection_interval": 60
},
"netstat": {
"measurement": [
"tcp_established",
"tcp_time_wait"
],
"metrics_collection_interval": 60
},
"processes": {
"measurement": [
"blocked",
"running",
"total",
"dead"
]
},
"statsd": {
"metrics_aggregation_interval": 60,
"metrics_collection_interval": 10,
"service_address": ":8125"
},
"swap": {
"measurement": [
"swap_used_percent"
],
"metrics_collection_interval": 60
}
}
}
}
Post Installation
For further customizing and securing the appliance see Post Installation Tasks.
Creating Users
To add users you will first Create an Organization and then Add Storage.
Setting Up Storage
Log out from the Appliance Admin, appladmin user, and log back in as the user you just created.
You will first see the “Add Storage Provider” screen. You have to add storage before you can continue.
Select your provider and follow the instructions on the next couple of screens. See the next section for information on setting up Amazon S3 storage.
Setting Up Amazon S3 Storage
After logging into the organization you will be prompted to register your cloud storage provider. Choose the provider (for example, Amazon S3) and click Continue to proceed.
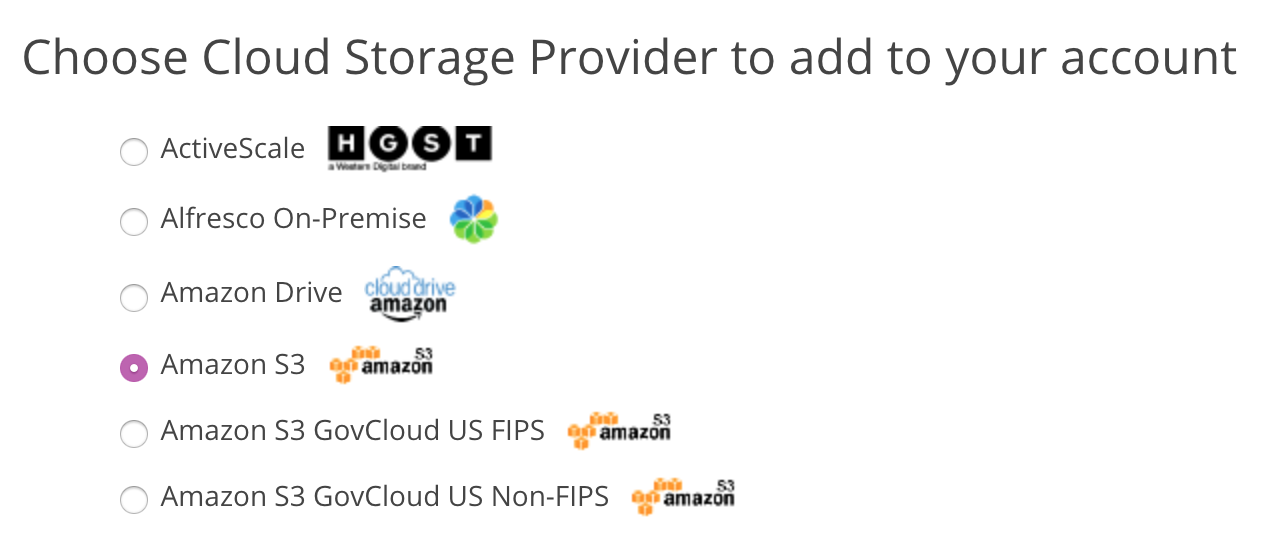
Amazon S3 Provider
Enter your S3 Access key and secret to continue:
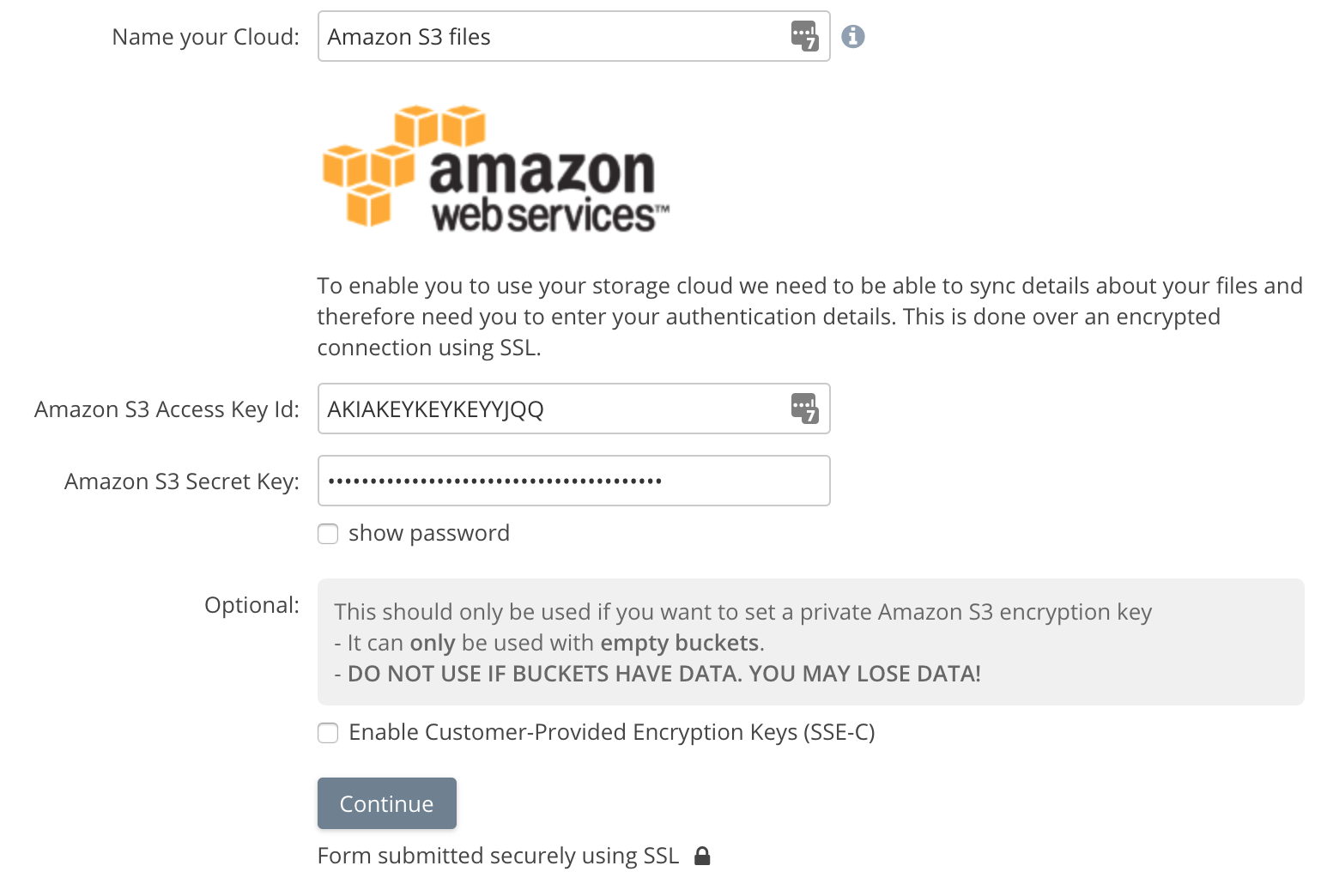
The credentials are validated and a list of buckets in the account are returned. Select the buckets you wish to be indexed. We recommend not using buckets with existing production data for the initial trial.
Select and create a new bucket for default data (at the bottom) before selecting Continue. You are then ready to add users!
Appliance Backup
Single-node appliances can be easily backed up as EC2 Snapshots.
For general information on appliance and database backup strategies see Appliance Backups.
Creating a Backup
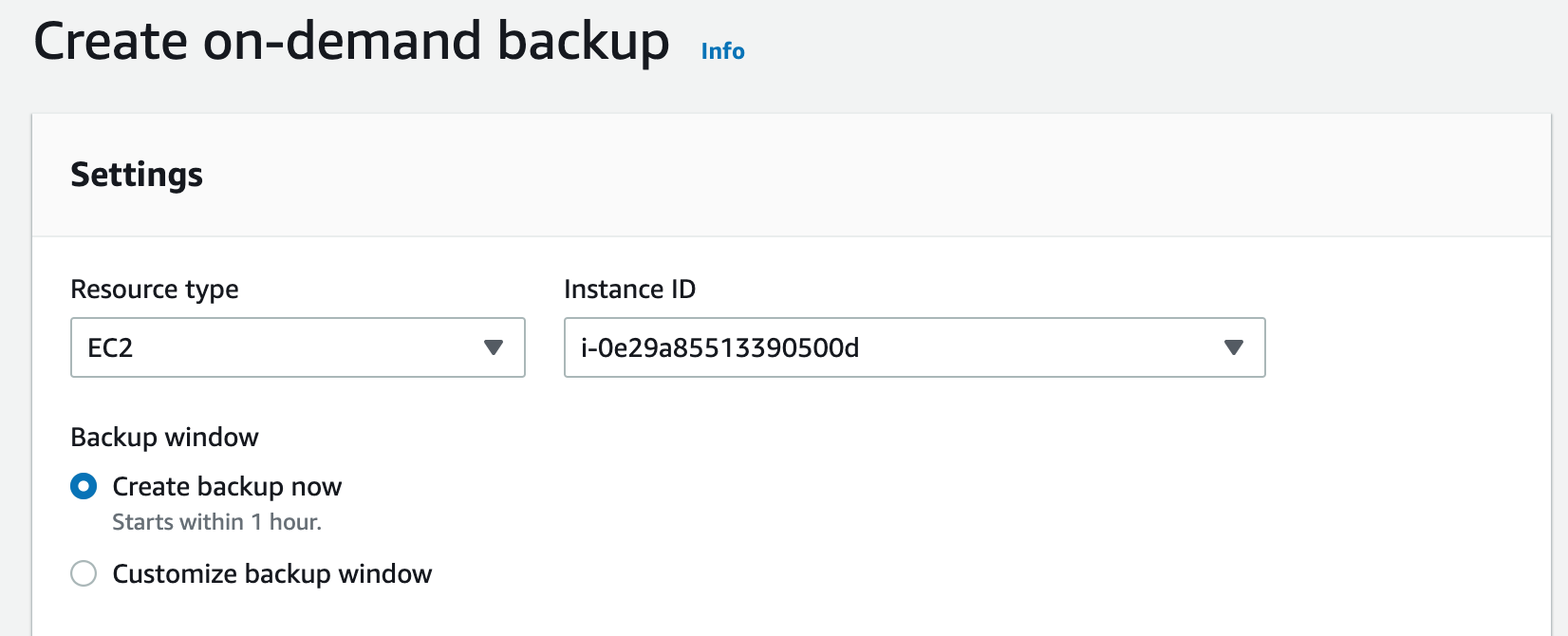
To create an appliance backup on demand navigate to the AWS Backup dashboard.
Choose Create an on-demand backup and follow the prompts to back up the EC2 Resource you just created.
Select Create on-demand backup. A backup of a 150 GB instance should take less than 10 minutes.
Automating Backups
Backups can be automated through the AWS Backup service.
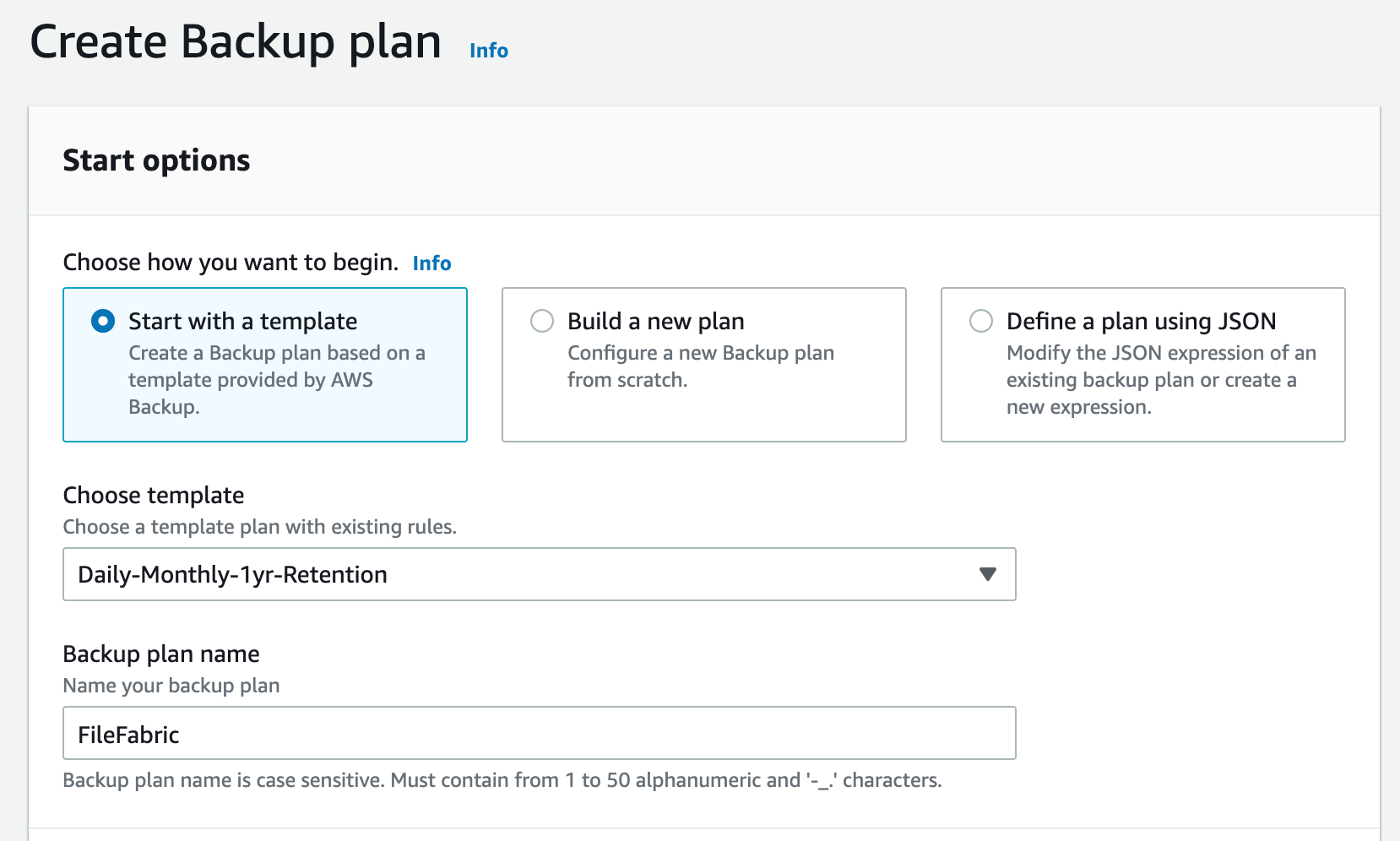
From the AWS Backup dashboard in your region choose Create a Backup plan to bring up the Start options.
Select Start with a template and choose an appropriate template. For example Daily-Yearly-1yr-Retention. Enter a plan name and select Create plan.
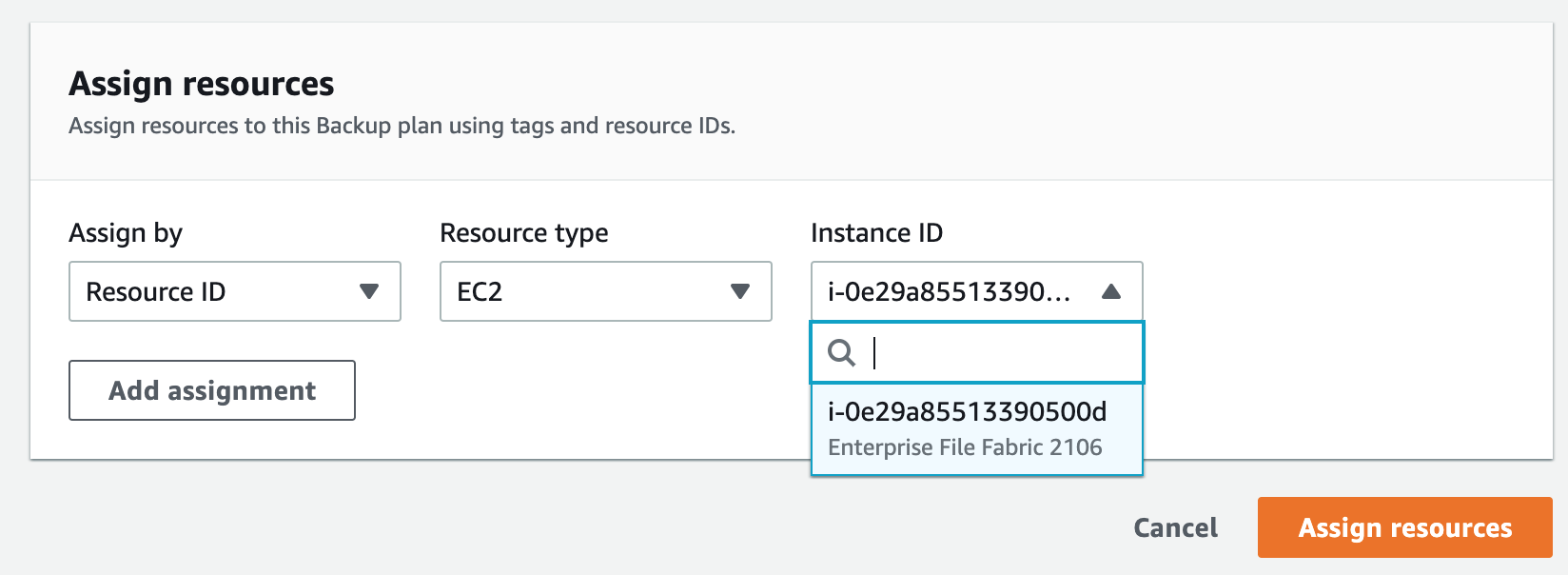
Once the backup plan is created, navigate to it and select Assign Resources.
Enter a name, choose Assign by Resource ID, and then select the instance you want to be backed up. Then choose Assign Resources.
For offsite backups select a Backup Rule and choose a region for Copy to destination:
Restore Backup
On instance or service failure, the backup is used to restore the appliance to a new instance.
Navigate to the AWS Backup dashboard and select Restore Backup.
Choose the “Protected Resource” to be covered. This will then show backups that are available and when they were created.
Choose a backup and select Restore.
You will be prompted for an instance type and network settings but you can leave the defaults as-is. They are the settings of the instance at the time it was backed up.
Once the backup has been restored log into the new external IP address to verify the instance has completed startup. Assign the Elastic IP Address to the recovered instance.
Users can start using the recovered instance immediately.
Next, update the backup plan to back up this new instance going forward.
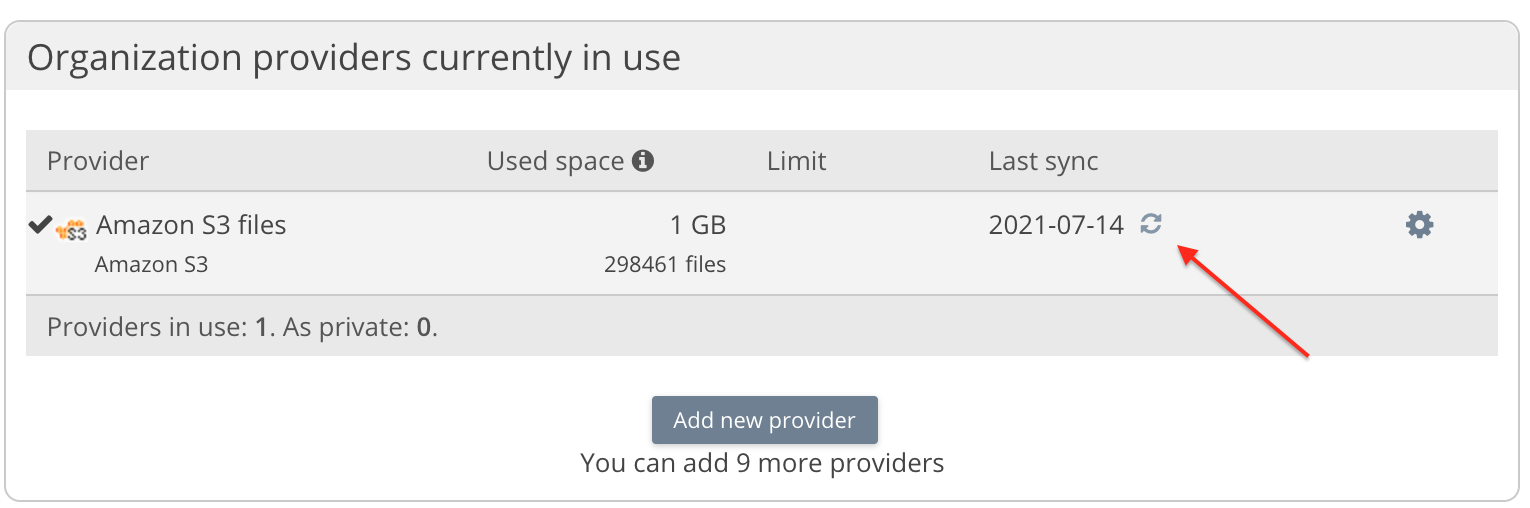
You can then recover any missed storage metadata by running a resync on each provider. Log in as an administrator to the web app and select Dashboard. Select the sync icon as shown to start a resync.
Routine Maintenance
Rotating Credentials
To rotate Amazon S3 storage keys see Amazon S3 Provider.
Upgrades
Upgrades for instances running on the AWS Cloud are delivered through RPM packages via our curated repository. Always follow the upgrade documentation as sometimes additional steps post-upgrade are required.
You will be notified through your designated support contact when new versions of the software or security patches for third-party components are available.
Licenses
Licenses are provided upon renewal. To apply licenses see Activating your License.
Support
Contact Nasuni Support through email at support@nasuni.com or through the Support Portal.