Table of Contents
Governance Settings
last updated on April 27, 2020
1 User Management
Users and user roles can be controlled directly by the Cloud Administrator when setting up the Cloud File Server.
2 Permissions and access control
Once shared folders for the Cloud File Server have been added, the Cloud File Server Admin can control access to folders and sub folders using an access control list. If a user has no permission to a folder the folder is not displayed at all in their file tree.
FAQ: We often get asked if we support Active Directory integration. We support Active Directory integration, and this enables single sign on and group permissions federation.
3 Notifications
The Access Anywhere Admin can setup Audit Watch notifications. Notifications are based upon rules that are invoked on file events. If a file of a certain description, file name or extension is uploaded, updated, viewed etc, then the nominated users can receive notification alerts.
4 Event Auditing and Other Governance Options
Event logging is built into Access Anywhere and it works above any storage provider that is mapped to Access Anywhere. Which types of events are logged can be controlled by the org. admin from the Security tab of the Policies page:
5 Displaying and Filtering Event Logs
The org. admin can view the events belonging to the org. on the Audit Events Log page which is accessed from the admin's Organization pull-down menu:
There are five filters:
Search logs
The contents of the Log field will be filtered by the value you provide here without regard to case.
Type
Events are classified by type. You can filter by any single type or allow all types:
You can also filter by the user whose action caused the events, the date or range of dates during which the events occurred, and the tool that was used.

The date range is inclusive. To select events for a specific date set that date as both the From date and the To date.
You can set values in any or all of the five filters and then search. The filters are logically combined so that only events that qualify for all of the filter values that have been set are displayed.
Use the Search button at the bottom left of the page to re-filter the results after you change a filter value. You can reset all of the filters to their default (no value) state by clicking in the link under the Search button.

Exporting Audit Logs
Your filtered set of audit log entries can be downloaded in four forms:
- Excel workbook
- .csv file
- .zip archive.
- PDF file as a formatted report
Access these three options from the Export pulldown near the top of the Audit Event Logs page:

Archiving and Erasing Audit Logs
Because audit log entries accumulate quickly you will probably want to archive the entries from time to time and then erase them. You can access archiving and deletion features from the Options pulldown near the top of the Audit Event Logs page:
To archive the audit log entries, select Archive from the pulldown menu and a confirmation box will be displayed:
Select a folder to archive the logs to.
Click on Archive to proceed or Cancel to cancel.
If you proceed a background task will be created which will create a zip file containing the audit log entries. If you care to inspect the background task, find its entry on the Tasks tab of the File Manager page:
Audit logs archives will be placed by the background task into the directory chosen when archiving was started.
Select Erase Logs from the pulldown menu to erase old audit log entries.
When you erase audit log entries they will no longer be available from Access Anywhere. If you need a historical record, archive these entries before you delete them and be sure that the archive job has completed successfully prior to proceeding.
When you erase audit log entries, only entries from before a date that you select will be erased:
After you have selected the date click on Erase to proceed or click on Cancel if you have changed your mind.
Tracing Downloads by Watermark
The Access Anywhere provides a Watermarking feature that affixes a random watermark code to downloaded PDF files. You may sometimes want to learn the details of when a watermarked file was downloaded. To do this, click on the Watermarking Logs link near the top of the Audit Event Logs page:
This will take you to the Watermarking Logs page:
When this page loads it displays a list of all watermarked file downloads in reverse chronological order. To search for downloads for files with a specific watermark code, enter some or all of the code in the Watermark Code text box and click on Filter. The text you entered will be used without regard for case to filter the watermark downloads by the code in the first column. You can clear the filter with the “Clear filter” button.
Also See
6 Recording GEO locations
GEO locations are recorded with regards to where a file was uploaded from and also where a file was uploaded to. This can ensure companies comply with electronic data laws and international compliance regimes
7 Disable File Sharing
The Access Anywhere Admin can disable any sharing or collaboration features of Access Anywhere entirely by disabling the ability for any user to do any form of file sharing or collaboration from Access Anywhere policies page.
8 Controlling User Access to Storage
As the Organization, or individual users, may (if configured) user other storage , it is preferable for these to be controlled as part of Access Anywhere rollout in a company. If available this will also enable that auditing, event logging etc for such storage. The Access Anywhere admin can decide which storage a user can add.
For example if each user has a corporate Google Apps account, then the Admin can enable users to add this directly (with any use also being monitored and audited.
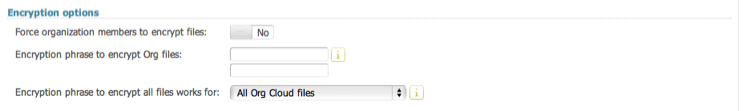
9 Encryption options
Cloud Admins can choose for all files to be encrypted when stored on private / cloud storage. This encryption is AES 256 bit military grade encryption.
See the encryption section for further information.