Table of Contents
Nasuni Access Anywhere Security
Updated on Mar 19, 2024
Access Anywhere provides content collaboration, federation, governance and data management features.
See Also
Security related features include:
Encryption - Data in Transit
HTTPS is configured by default for all users.
A commercial server that uses HTTPS must have a public key certificate issued that verifies the entity. The end-user can verify the entity by clicking on the HTTPS icon from the browser.
Clients should connect to the server using a URL that starts with HTTPS. (This is the default). A valid certificate is required.
Administrators should also connect to storage providers using HTTPS. For storage providers with a fixed endpoint including AWS S3, Azure, Google Cloud Storage the Access Anywhere server always uses HTTPS.
Encryption - Data at Rest
Customer data is stored on storage services controlled by you. It is not stored on the appliance.
Encryption Algorithm
The Access Anywhere server can be used to encrypt data transmitted to any storage provider that is under management by the solution. The plarform uses AES-256 encryption using the Rijndael cipher, with Cipher Block Chaining (CBC) where the block size is 16 bytes. The cipher Rijndael consists of:
- an initial Round Key addition
- Nr-1Rounds
- a final round.
The chaining variable goes into the input and the message block goes into the Cipher Key. The likelihood of recovering a file that has been encrypted using our encryption is fairly remote. The most efficient key-recovery attack for Rijndael is exhaustive key search. The expected effort of exhaustive key search depends on the length of the Cipher Key and for a 16-byte key, 2127 applications of Rijndael;
Any AES-256 decryption tool that supports the Rijndael cipher with 16 byte blocksizes can be used to un-encrypt files. We also provide free desktop decryption tools for Mac, Windows and Linux that enable the decryption of a file if you download it directly from a mapped cloud ie. without any access to the service.
View the online NIST certification.
See also FIPS U.S. Federal Government Validation of Access Anywhere™ Cryptographic Algorithm.
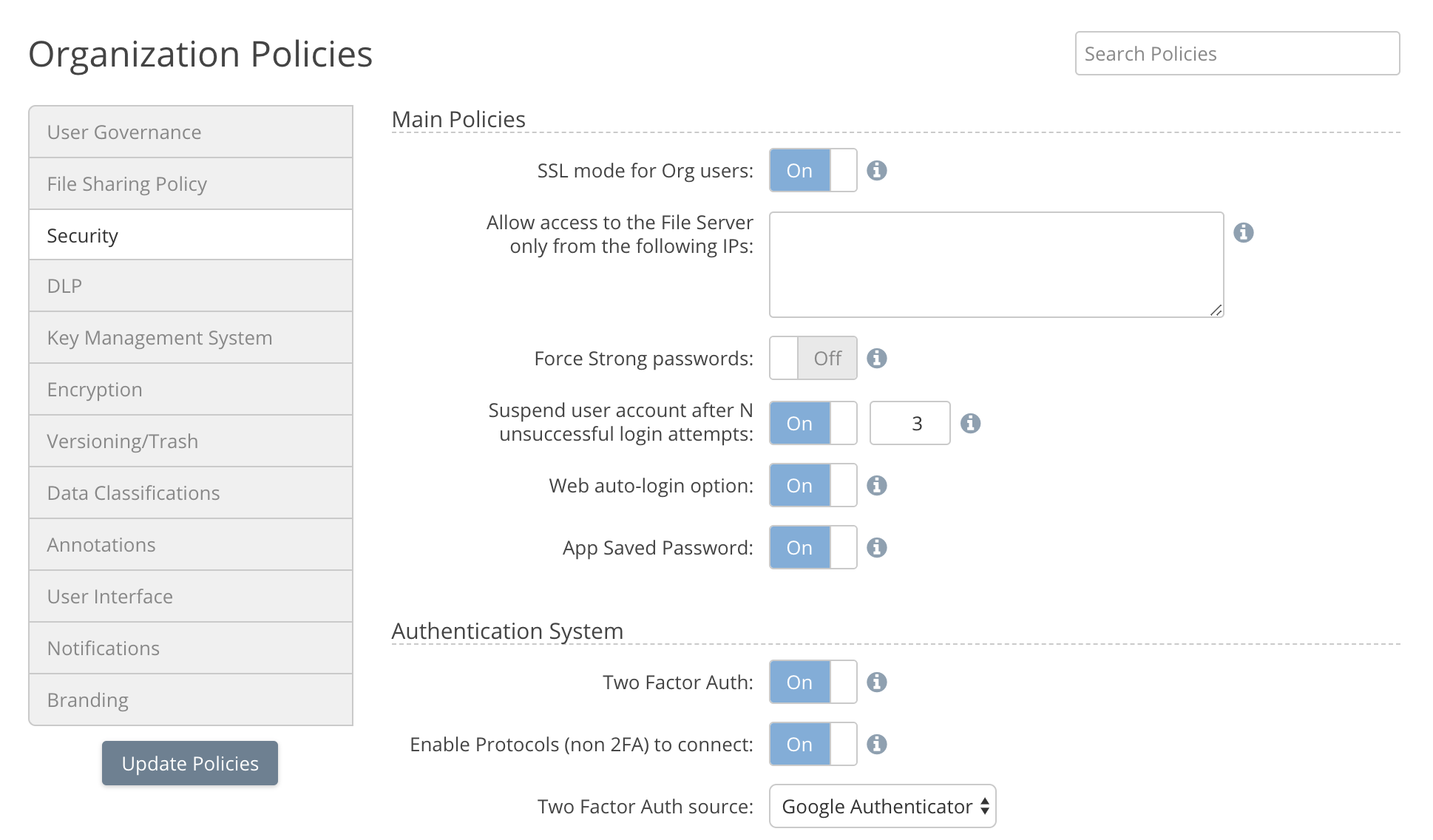
Identity Authentication
Clients can be authenticated against the internal user database or any directory service. Nasuni Access Anywhere includes out of the box support for Microsoft Active Directory, and services that support LDAP and SAML. Once authenticated clients use the authentication token for the remainder of the session.
Two-factor authentication may also be required with the options of Google Authentication, an emailed code, or a shared secret supported.
Our staff has no way to access a password as it is stored encrypted. There is a means to access meta-data in the logs and database related to an account if a user requests help with a problem, and this is only ever used if a user requests us to look at a problem or issue with an account. Even so, this still requires an Administrator to authorise access, and it still does not grant any access to any encrypted passwords.
If a storage provider supports OAuth, which is a mechanism to connect to a Cloud Provider without revealing password details, then Access Anywhere uses this delegation mechanism to access the resource. For storage providers that don't use OAuth, authentication details are stored encrypted (AES-256 Rijndael CBC with salt).
For more information see Identity and Access Management.
Data Loss Protection
Documents can be securely shared in a number of ways:
- Documents can be encrypted on upload using 256 bit AES security. The private key is not stored on the platform and only known by the user.
- Private links can be created for documents and these can be combined with passwords to secure the document.
- Links can be set to be time expired and/or combined with private links and password for further additional document security.
- Watermarks unique to each file preview or shared file download can be added to enable tracing back how a file was leaked.
- Content Discovery monitors documents for sensitive data which can generate an email, quarantine, or initiate a workflow.
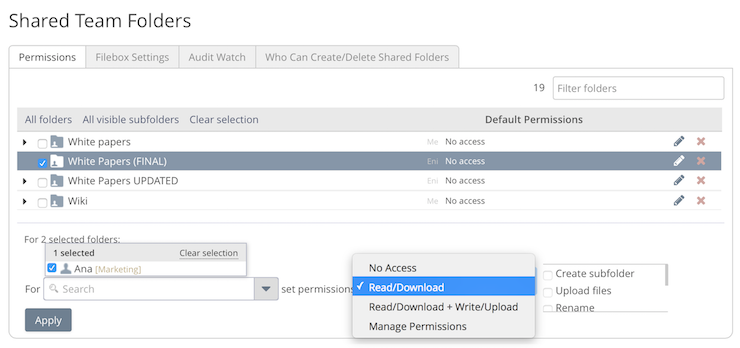
Access Control Security
The platform supports Access Control Permissions at a Role, User, or folder level for shared folders. The Permissions can be taken from Active Directory / LDAP if single sign-on is being used.
Restrict by IP Address
The platform supports the ability to whitelist or blacklist IP addresses to allow / deny connections. This can be done at the Organization level (tenant) or on a per user basis.
For more information see IP Whitelisting / Blacklisting.
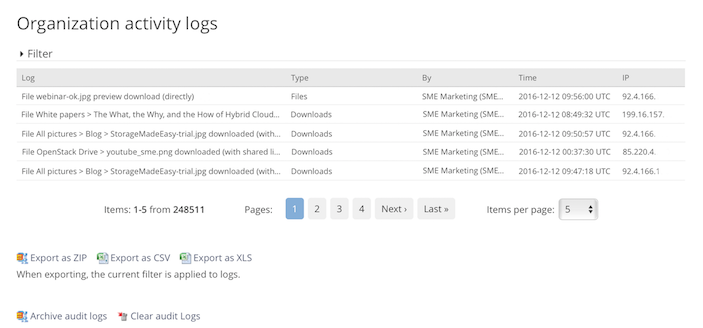
Audit Security
All file events that occur when using Access Anywhere are recorded.
Reports can be accessed online, archived, and also exported as .cvs or excel files or the audit events can be configured to be output in syslog format so that log aggregators such as Splunk can be used to monitor / collate the resultant logs.
Governance Options
There are comprehensive governance / compliance / security options which can be configured by an Administrator.
Acceptable Use Policies
Acceptable use policies allow organizations to present policies and optionally required acceptance for access to the system. Policy acceptance is logged and can also be required by users downloading shared files and folders.
See Registration & Acceptable Use Policies for more information.
Bring your own Device security
The Administrator controls which devices and access clients that each user can connect from. By default all devices and access clients are enabled.
The Admin can entirely disable a user or just choose to disable access from any of the devices/access clients from the users settings instantly disabling user access.
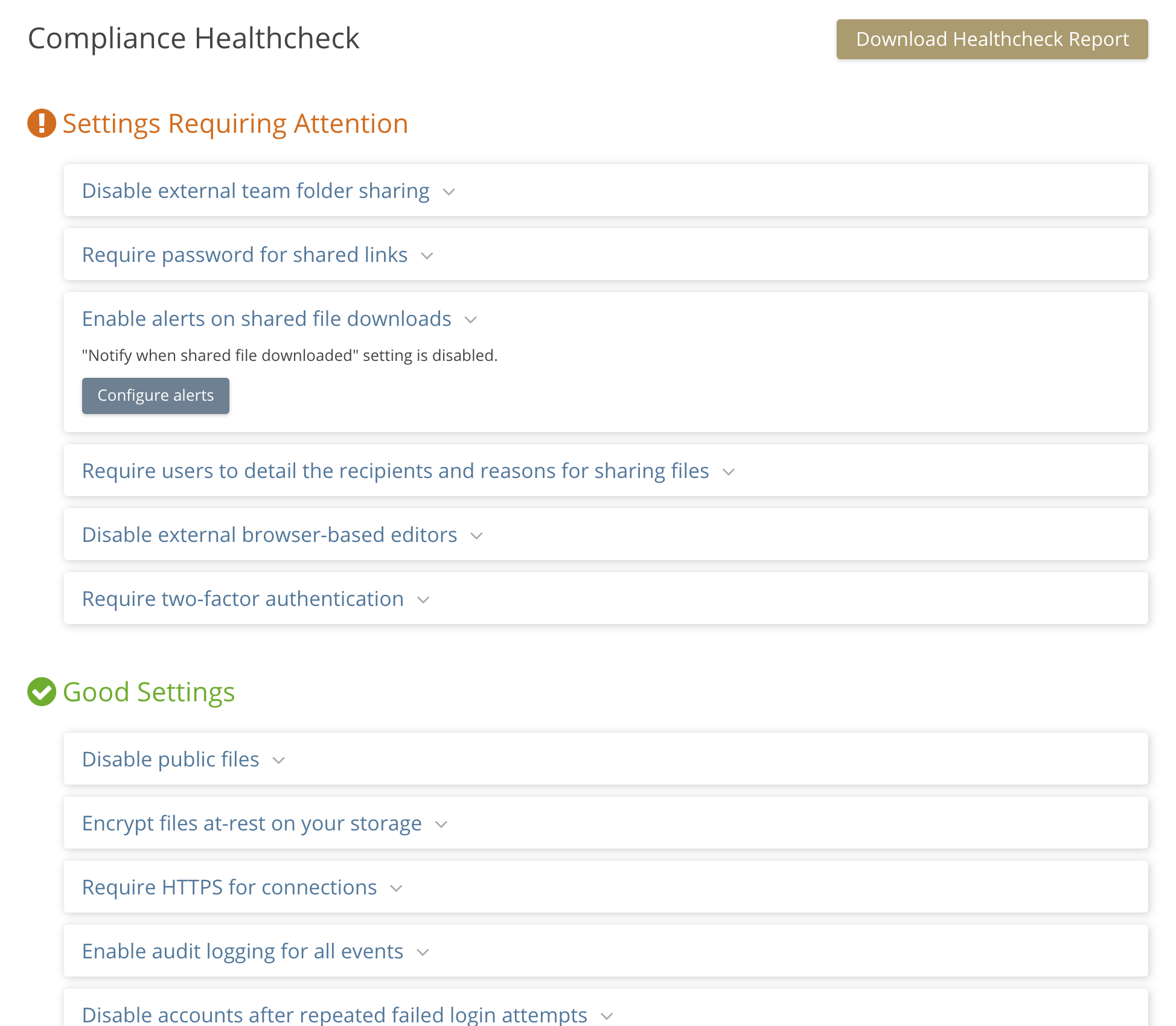
Compliance Report
The compliance report recommends settings that could be changed to enhance security. The user can jump from the online report directly to where the setting can be changed.
Data Security
In addition to encryption the solution includes a number of features for data security:
- Trash - Folders and files that are updated or deleted are saved in trash and can be restored.
- Versions - Unlimited or limited versions of files can be saved.
- Disaster Recovery - The ForeverFile™ archive is a backup, disaster recovery and ransomware protection feature that continuously protects data, wherever it is stored. For each primary storage provider that is being protected, a separate secondary or Backup provider is configured. For maximum availability the backup cloud should be located in another data center. It could also be with different cloud vendor, storage technology or tier.
- Antivirus - See Virus Scanning Protection.
Product Design and Testing
The platform is developed using the OWASP principle of Security by Design. Each product release, service pack, and patch is security audited and tested through the use of multiple third party security products.
Our own hosted service, which features the latest iteration of bug fixes and features, is security tested daily.